Permission Explanation
Linux file permissions are a fundamental aspect of securing a Unix-like operating system. These permissions control who can read, write, or execute files, ensuring the system remains safe and operational. Linux file systems use three primary types of permissions: read (r), write (w), and execute (x). These permissions are divided into three groups, determining access for the user/owner (u), the group (g), and others (o).
Example:
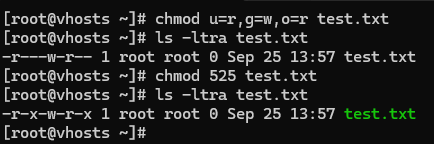
You can represent permissions in two formats: numeric (octal) or symbolic. You can check the above example. For instance, the numeric value 764 corresponds to the symbolic notation rwxrw-r-. The leftmost digit (7 or rwx) defines the user/owner permissions. The middle digit (6 or rw-) represents group permissions, and the rightmost digit (4 or r-) defines the permissions for others. The table below shows how numeric values translate into their symbolic counterparts:
| Numeric | Symbolic | Permission |
| 0 | — | none |
| 1 | –x | execute only |
| 2 | -w- | write only |
| 3 | -wx | write and execute |
| 4 | r– | read only |
| 5 | r-x | read and execute |
| 6 | rw- | read and write |
| 7 | rwx | read, write and execute |
Special Permissions
A fourth (leading) digit in the numeric notation denotes special modes or permissions, such as setuid, setgid, and the sticky bit. In symbolic notation, these bits appear within the corresponding triads: the setuid bit is part of the user triad, the setgid bit is part of the group triad, and the sticky bit is part of the others triad. The table below shows the numeric values and their corresponding symbolic representations for these special permissions:
| Special Mode | Numeric | Symbolic | Executable |
| setuid | 4 | third character in the user triad: | s (also executable), S (not executable) |
| setgid | 2 | third character in the group triad: | s (also executable), S (not executable) |
| sticky bit | 1 | third character in the others triad: | t (also executable), (not executable) |
Understanding Linux file permissions is essential for both system security and management. By configuring these permissions correctly, you can prevent unauthorized access while maintaining proper file functionality.
References:
Other Calculators



